Intel is working with US startup Eclypsium to reduce the vulnerability of firmware throughout an organisation, including its cloud links. This pairs security capabilities built into Intel silicon with advanced defences against firmware threats.
Intel Security Essentials provide a built-in foundation for improved security features and are available across Intel processor lines. The Eclypsium Platform, now generally available, builds upon Intel’s foundation by analyzing the system configuration and ensuring the latest firmware is deployed. With Eclypsium, the end user can see the status of their firmware patch levels, gain visibility into firmware misconfigurations, and validate the integrity of Intel systems as part of the supply chain, even through the cloud.
This can also help protect against 'Evil Maid' attacks against devices such as laptops or phones that are left unattended, for example in a hotel room or at an airport. This uses a USB-stick to compromise the firmware with a fake password prompt identical to the original. Once the password is input, the compromised firmware sends the password to the attacker and removes itself after a reboot. However, this nodes need the hacker to return to the device a second time to steal the now-accessible data.
“With security features built into the hardware, Intel delivers a ‘chain of trust’ rooted in silicon that makes the device and extended network more trustworthy and secure,” said Yuriy Bulygin, CEO of Eclypsium. “We are pleased to be working with them to extend that chain of trust for the firmware layer, and therefore across the supply chain, while enabling leading hardware OEMs to deliver the right patches and more secure hardware configurations to the market.”
“Security sensitive organizations need to be able to inspect these low-level technologies to look for signs of malicious activity,” said Window Snyder, Chief Software Security Officer and General Manager, Platform Security Division at Intel.
As well as protection against Evil Maid attacks, Intel and Eclypsium are demonstrating a number of use cases:
“With security features built into the hardware, Intel delivers a ‘chain of trust’ rooted in silicon that makes the device and extended network more trustworthy and secure,” said Yuriy Bulygin, CEO of Eclypsium. “We are pleased to be working with them to extend that chain of trust for the firmware layer, and therefore across the supply chain, while enabling leading hardware OEMs to deliver the right patches and more secure hardware configurations to the market.”
“Security sensitive organizations need to be able to inspect these low-level technologies to look for signs of malicious activity,” said Window Snyder, Chief Software Security Officer and General Manager, Platform Security Division at Intel.
As well as protection against Evil Maid attacks, Intel and Eclypsium are demonstrating a number of use cases:
- Firmware Visibility and Patch Management - Visibility of firmware versions across hardware components and centralised patch updates.
- Protection From Supply Chain Attacks – Find firmware that has been compromised in the hardware supply chain even before deployment.
- Protecting Cloud Infrastructure – Help protect cloud and bare-metal infrastructure from implants at the firmware level or software-level attacks that can spread to the firmware.
- Verifying Device Integrity After Infection - Bring firmware security into the workflow to help ensure devices are clean at the firmware level before re-imaging.
eclypsium.com


 .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
. 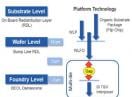 .
.  .
.  .
. 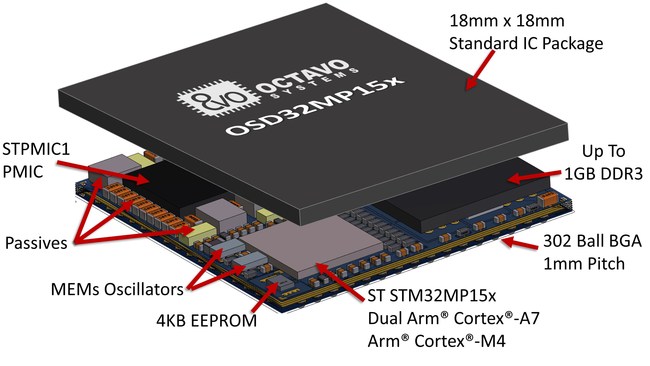 The OSD32MP1 integrates the STM32MP1, DDR, PMIC, EEPROM, Oscillators, and Passives into a single BGA package that is 18mm X 18mm.
The OSD32MP1 integrates the STM32MP1, DDR, PMIC, EEPROM, Oscillators, and Passives into a single BGA package that is 18mm X 18mm.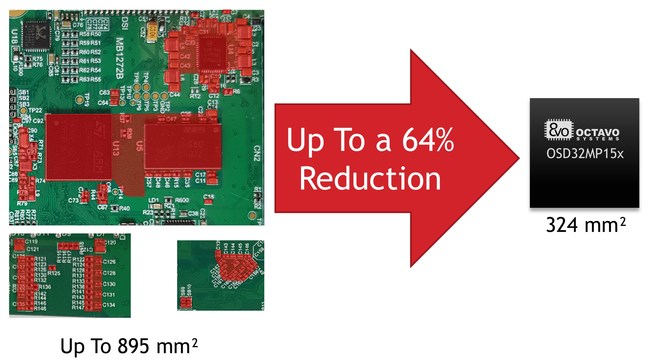 At only 18mm on a side, the OSD32MP1 packs an entire STM32MP1 system in a package the same size as the processor itself saving designers up to 64% in PCB area.
At only 18mm on a side, the OSD32MP1 packs an entire STM32MP1 system in a package the same size as the processor itself saving designers up to 64% in PCB area. .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.  .
.